Strictly Necessary
These cookies are required for the website to function properly. They do not collect data for advertising purposes and cannot be disabled, as this would break the site's basic functionality.
Trusted Hub
A New Generation Secured Unified Authentication Gateway with Adaptive Intelligence |
Trusted HubConcept of Trusted Hub, how it work ? how it help to secure and centralize your password when you login? |
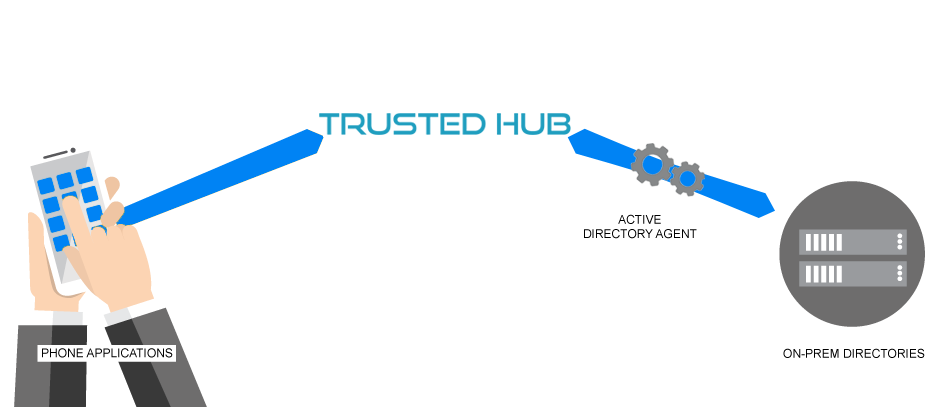
A secure way to identity management. Simplify the user ID credential of multiple applications to a centralized pool of user source



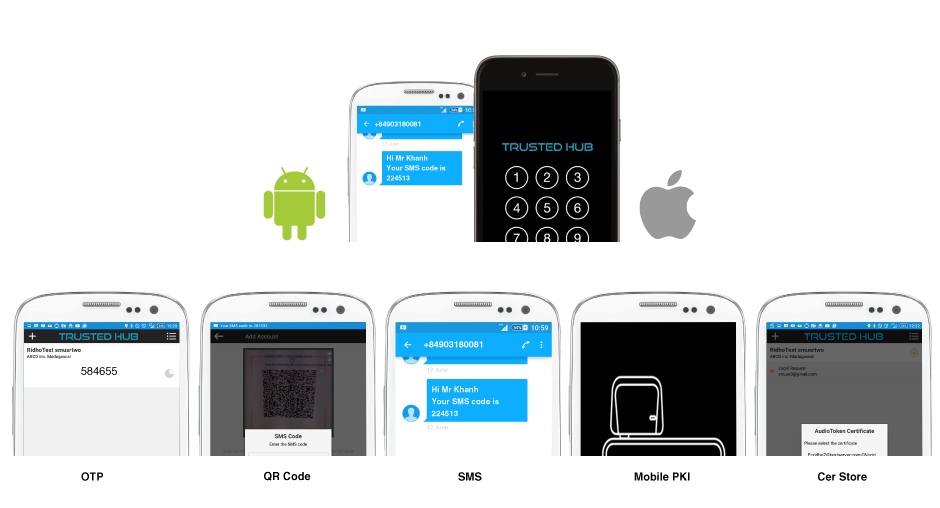
Software
|
Hardware
|
Out of band
|
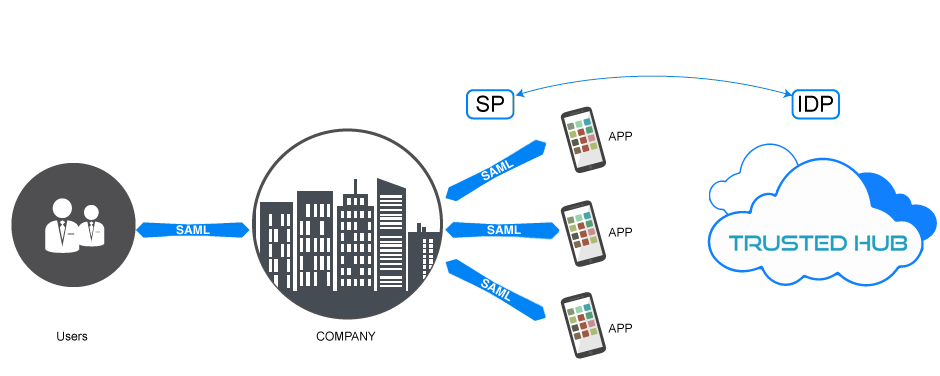
Federated identity management with multifactor authentication options

Access All Application with Single Identity
Enforce policy in multiple domain |
Integrated XIO Integration, With Password Privacy
Enforce policy in multiple domain |
Secure and Configurable Access
Enforce policy in multiple domain |
A New Approach to Mobility - Now you can centrally manage people, devices and access to web and mobile apps, to achieve better security and efficiency
BYOD or Bring your own device offer flexible option for end user to utilize their own devices as security tokens
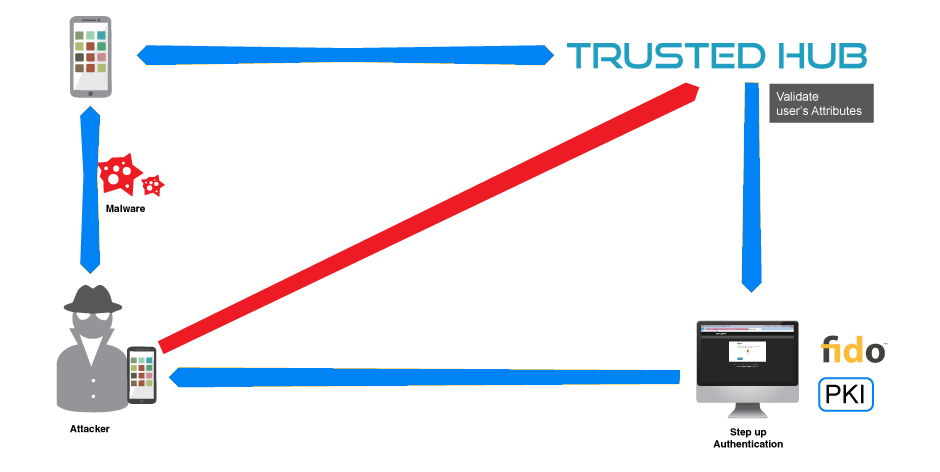
In Mobile Platforms (BYOD), not all authentication solutions offers higher security to ensure user credentials are protected. In Trusted Hub, a user previously processed is secured with its own tokenization technology. Security keys we generated and binded with the device. Key life cycle will cover its revocation for disposal.

Trusted Hub allows BYOD (Bring Your Own Devices) to be used as security token user source.